Check Point SSL Network Extender Help
Introduction
Welcome to the Check Point SSL Network Extender.
The SSL (Secure Socket Layer) Network Extender is a simple-to-implement remote access solution. It provides a secure connectivity framework to ensure that remote access to the corporate network is securely enabled.
The SSL Network Extender uses ActiveX technology to enable you to enjoy the benefits of Check Point's VPN, via your browser.
Learn more...
Configuring Microsoft Internet Explorer
Downloading and Connecting the Client
Importing a Client Certificate to Internet Explorer
Removing an Imported Certificate
System Requirements
The system requirements are listed below:
- Microsoft® Windows Pro/XP Home Edition and Pro
- Microsoft® Windows Vista
- Microsoft® Internet Explorer 5.0 or higher
Note: To upgrade to the latest version of Internet Explorer, visit the Microsoft Web site at http://www.microsoft.com/ie.
Configuring Microsoft® Internet Explorer
Check Point SSL Network Extender uses ActiveX controls and cookies to connect to applications via the Internet. These enabling technologies require specific browser configuration to ensure that the applications are installed and work properly on your computer. Please follow the directions below to configure your browser.
1. Determine which version of Internet Explorer you are using.
a. Open Internet Explorer.
b. On the Help menu, click About Internet Explorer to open the About Internet Explorer dialog box.
c. Look for the line labeled Version: and note the first three digits.
For Example: Version: 5.50.4807.2300. The bolded digits indicate that the Internet Explorer version is 5.50. You should, therefore, use the "Configuring Internet Explorer 5.x" instructions.
2. Click the appropriate link to learn how to configure your version of Internet Explorer.
After you configure Internet Explorer, it will have the correct security settings to download, install, and run the SSL Network Extender.
Configuring Microsoft® Internet Explorer 5.x
To configure Microsoft® Internet Explorer 5.x, proceed as follows:
- Open Internet Explorer. On the Tools menu, click Internet Options to open the Internet Options dialog box.
- Click the Security tab. Make sure that you are in the Internet Web content zone and that the security level for this zone is set to Medium (the default setting) or Low.
- If you are not sure whether your security options are correct, click Default Level to set the zone to Medium (recommended).
- If you are an advanced user who wants to customize your security settings, click Custom Level to open the Security Settings dialog box. To use Check Point SSL Network Extender you must enable the following options.
a. Enable the following ActiveX controls and plug-ins options:
- Download signed ActiveX
controls
- Run ActiveX controls and plug-ins
- Script ActiveX controls marked safe for scripting
b. Enable the Active scripting option, under the Scripting settings.
- When you are done, click OK, and then click Yes to confirm the changes.
- Click OK to close the Security Settings dialog box.
- Click OK to close the Internet Options dialog box.
- Exit Internet Explorer.
Configuring Microsoft® Internet Explorer 6.x
To configure Microsoft® Internet Explorer 6.x, proceed as follows:
- Open Internet Explorer. On the Tools menu, click Internet Options to open the Internet Options dialog box.
- Click the Security tab. Make sure that you are in the Internet Web content zone and that the security level for this zone is set to Medium (the default setting) or Low.
- If you are not sure whether your security options are correct, click Default Level to set the zone to Medium (recommended).
- If you are an advanced user who wants to customize your security settings, click Custom Level to open the Security Settings dialog box. To use Check Point SSL Network Extender you must enable the following options.
a. Enable the following ActiveX controls and plug-ins options:
- Download signed ActiveX
controls
- Run ActiveX controls and plug-ins
- Script ActiveX controls marked safe for scripting
b. Select Prompt for the following ActiveX controls and plug-ins options:
- Download unsigned ActiveX
controls
- Initialize and script ActiveX controls not marked as safe
c. Enable the Active scripting option under the Scripting settings.
- When you are done, click OK, and then click Yes to confirm the changes.
- Click the Privacy tab on the Internet Options dialog box, and then click Advanced to open the Advanced Privacy Settings dialog box.
- Make sure that Override automatic cookie handling and Always allow session cookies are selected, and then click OK to close the Security Settings dialog box.
- Click OK to close the Internet Options dialog box.
- Exit Internet Explorer.
About ActiveX Controls
ActiveX controls are software modules, based on Microsoft's Component Object Model (COM) architecture. They add functionality to software applications by seamlessly incorporating pre-made modules with the basic software package.
On the Internet, ActiveX controls can be linked to Web pages and downloaded by an ActiveX-compliant browser. ActiveX controls turn Web pages into software pages that perform like any other program launched from a server.
Check Point uses ActiveX controls in its applications, and you must download the specific ActiveX components required for each application. Once these components are loaded, you do not need to download them again unless upgrades or updates become available.
Note: You must have Administrator rights to install or uninstall software on Windows XP Professional, as well as on the Windows 2000 operating systems.
Downloading and Connecting the Client
The following section discusses how to download and connect the SSL Network Extender.
To download the Client:
1. Using Internet Explorer, type in the URL, assigned by the system administrator. The format is https://xxx.xxx.xxx. The Security Alert window may be displayed.
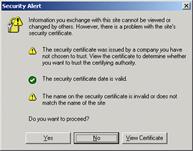
Security Alert Window
The site’s security certificate has been issued by an authority that you have not designated as a trusted CA. Before you connect to this server, you must trust the CA that signed the server certificate. (The system administrator can define which CAs may be trusted by the user.) You can view the certificate in order to decide if you wish to proceed.
NOTE: The administrator can direct the user to the URL, http://< mngmt IP>:18264, to install this CA certificate, thereby establishing trust, and avoiding future displays of this message. The Install this CA Certificate link is shown in the following figure.

Install this CA Certificate
2. Click Yes. If the authentication scheme, configured, is User Password Only, the following SSL Network Extender Login window is displayed.
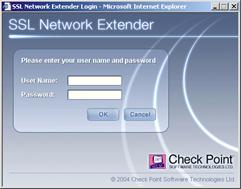
SSL Network Extender Login Window
3. Enter the User Name and Password and click OK. The VeriSign Certificate message is displayed.
4. If the authentication scheme, configured, is Certificate without Enrollment, and the user already has a certificate, the VeriSign Certificate message is displayed. If the user does not already have a certificate, access is denied.
5. If the authentication scheme, configured, is Certificate with Enrollment, and the user does not already have a certificate, the Enrollment window is displayed:
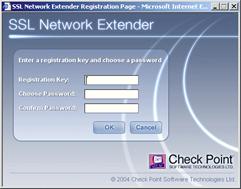
Enrollment window
6. The user enters his/her Registration Key, selects a PKCS#12 Password and clicks Enroll. The PKCS#12 file is downloaded. The user should open the file and utilize the Microsoft Certificate Import wizard.
Importing a Client Certificate to Internet Explorer
Importing a client certificate to Internet Explorer is acceptable for allowing access to either a home PC with broadband access, or a corporate laptop with a dial-up connection. The client certificate will be automatically used by the browser, when connecting to an SSL Network Extender gateway.
To import a client certificate:
1. Open the downloaded PKCS#12 file. The Certificate Import Wizard window appears:
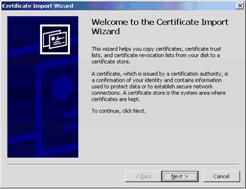
Certificate Import Wizard window
2. Click Next. The File to Import window appears:
File to Import window
The P12 file name is displayed.
3. Click Next. The Password window appears:
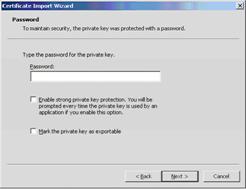
Password window
It is strongly recommended that the user enable Strong Private Key Protection. The user will then be prompted for consent/credentials, as configured, each time authentication is required. Otherwise, authentication will be fully transparent for the user.
4. Enter your password, click Next twice. If the user enabled Strong Private Key Protection, the Importing a New Private Exchange Key window appears:
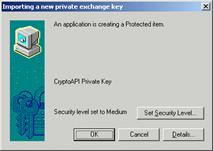
Importing a New Private Exchange Key window
5. If you click OK, the Security Level is assigned the default value Medium, and the user will be asked to consent each time his/her certificate is required for authentication.
6. If you click Set Security Level, the Set Security Level window appears:
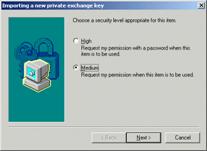
Set Security Level window
7. Select either High or Medium, and click Next.
8. Click Finish. The Import Successful window appears:
Import Successful window
9. Click OK.
10. Close and reopen your browser. You can now use the certificate that has now been imported for logging in.
11. If you are connecting to the SSL gateway for the first time, a VeriSign Certificate message appears, requesting the user’s consent to continue installation.
VeriSign Certificate Message
12. Click Yes. At first connection, the user is notified that the client will be associated with a specific gateway, and requested to confirm.
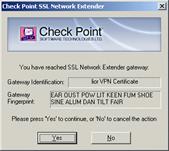
Client associated with specific gateway
The server certificate of the gateway is authenticated. If the system Administrator has sent the user a fingerprint, it is strongly recommended that the user verify that the server certificate fingerprint is identical to the fingerprint, sent to him/her.
The system Administrator can view and send the fingerprint of all server certificates, except those generated by using a registration key, via the Check Point Gateway Certificate List window.
13. Click Yes.
The ActiveX downloads. The client is connected, and you may work with the client as long as the window remains open, or minimized (to the System tray).
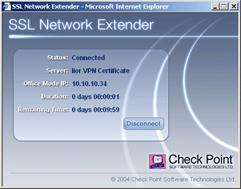
Client connected
Once the SSL Network Extender is initially installed, a new Windows service named Check Point SSL Network Extender and a new virtual network adapter are added. This new network adapter can be seen by typing ipconfig /all from the Command line.
NOTE: The settings of the adapter and the service must not be changed. IP assignment, renewal and release will be done automatically.
Both the virtual network adapter and the Check Point SSL Network Extender service are removed during the product uninstall.
NOTE: The Check Point SSL Network Extender service is dependent on both the virtual network adapter and the DHCP client service. Therefore, the DHCP client service must not be disabled on the user’s computer.
There is no need to reboot the client machine after the installation, upgrade, or uninstall of the product.
14. When you finish working, click Disconnect to terminate the session, or when the window is minimized, right-click the icon and click Disconnect. The window closes.
Uninstall on Disconnect
If the administrator has configured Uninstall on Disconnect to ask the user whether or not to uninstall, the user can configure Uninstall on Disconnect as follows.
To set Uninstall on Disconnect:
1. Click Disconnect. The Uninstall on Disconnect window is displayed, as shown in the following figure.
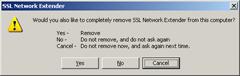
Uninstall on Disconnect
2. Click Yes, No or Cancel.
Clicking Yes results in removing the SSL Network Extender from the user’s computer.
Clicking No results in leaving the SSL Network Extender on the user’s computer. The Uninstall on Disconnect window will not be displayed the next time the user connects to the SSL Network Extender.
Clicking Cancel results in leaving the SSL Network Extender on the user’s computer. The Uninstall on Disconnect window will be displayed the next time the user connects to the SSL Network Extender.
Removing an Imported Certificate
If you imported a certificate to the browser, it will remain in storage until you manually remove it. It is strongly recommended that you remove the certificate from a browser that is not yours.
To remove the imported certificate:
1. In the Internet Options window, shown in the following figure, access the Content tab.
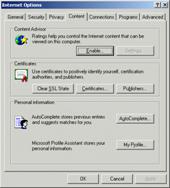
Internet Options window
2. Click Certificates. The Certificates window is displayed:
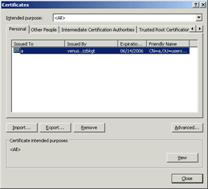
Certificates window
3. Select the certificate to be removed, and click Remove.
Troubleshooting
Tips on how to resolve issues that you may encounter are listed in the following table:
|
Issue |
Resolution |
|
The SSL Network Extender Gateway allows users to authenticate themselves via certificates. Therefore, when connecting to the SSL Network Extender Gateway, the following message may appear: “The Web site you want to view requests identification. Select the certificate to use when connecting.”
|
In order not to display this message to the users, two solutions are proposed: 1) On the client computer, access the Internet Explorer. Under Tools > Options > Security tab, select Internet Zone > Custom Level. In the Miscellaneous section, select Enable for the item Don’t prompt for client certificate selection when no certificates or only one certificate exists. Click OK. Click Yes on the Confirmation window. Click OK again. NOTE: This solution will change the behavior of the Internet Explorer for all Internet sites, so if better granularity is required, refer to the following solution. |
|
|
2) On the client computer, access the Internet Explorer. Under Tools > Options > Security tab, select Local intranet > Sites. You can now add the SSL Network Extender Gateway to the Local intranet zone, where the Client Authentication pop up will not appear. Click Advanced, and add the Gateway’s external IP or DNS name to the existing list. |
|
If the client computer has SecuRemote/ SecureClient software installed, and is configured to work in ‘transparent mode’, and its encryption domain contains SSL Network Extender Gateway, or otherwise overlaps with the SSL Network Extender encryption domain, the SSL Network Extender will not function properly. |
To resolve this, disable the overlapping site in SecuRemote/SecureClient.
|
|
If the client computer has SecuRemote/SecureClient software installed, and is configured to work in ‘connect mode’, and its encryption domain contains SSL Network Extender Gateway, or otherwise overlaps with the SSL Network Extender encryption domain, the SSL Network Extender will not function properly. |
To resolve this, verify that the flag allow_clear_traffic_while_disconnected is True (which is the default value). |
|
If the client computer has SecuRemote/SecureClient software installed, and is configured to work in ‘connect mode’, and has more than one site, and one of its encryption domains contains SSL Network Extender Gateway, or otherwise overlaps with the SSL Network Extender encryption domain, the SSL Network Extender will not function properly. |
To resolve this, disable the overlapping site in SecuRemote/SecureClient. |